
MMIXware: A RISC Computer for the Third Millennium
by Donald E. Knuth
Publisher: Springer 2004
ISBN/ASIN: 3540669388
ISBN-13: 9783540669388
Number of pages: 550
Description:
MMIX is a RISC computer designed by Donald Knuth to illustrate machine-level aspects of programming. This book constitutes a collection of programs written in CWEB that make MMIX a virtual reality. Among other utilities, an assembler converting MMIX symbolic files to MMIX objects and two simulators executing the programs in given object files are provided. The latest version of all programs can be downloaded from MMIX's home page. The book provides a complete documentation of the MMIX computer and its assembly language.
Download or read it online for free here:
Download link
(multiple PDF files)
Similar books
 Zen of Assembly Language: Volume I, Knowledge
Zen of Assembly Language: Volume I, Knowledgeby Michael Abrash - jagregory.com
This book unlocks the secrets of writing superb assembly-language code. It assumes that you're already familiar with assembly language, acquainted with the registers and instructions of the 8088, and with the use of one of the popular PC assemblers.
(8055 views)
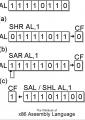 x86 Assembly
x86 Assembly- Wikibooks
This book covers assembly language programming for the x86 family of microprocessors. The objective is to teach how to program in x86 assembly, as well as the basic architecture of x86 processor family. The book for readers at the intermediate level.
(24500 views)
 Easy 6502
Easy 6502by Nick Morgan - GitHub
In this tiny e-book I'm going to show you how to get started writing 6502 assembly language. The 6502 processor was massive in the seventies and eighties, powering famous computers like the BBC Micro, Atari 2600, Commodore 64, Apple II, etc.
(10261 views)
 PC Assembly Language
PC Assembly Languageby Paul A. Carter
The book discusses how to program the 80386 and later processors in protected mode. The tutorial has extensive coverage of interfacing assembly and C code and so might be of interest to C programmers who want to learn about how C works under the hood.
(23003 views)